Fungsi Sistem Operasi
1. Sebagai Resource Manager /pengelola seluruh sumber daya system komputer
- Mengatur dan mengefisienkan penggunaan selluruh sumber daya komputer (computer resources)
- Tugas utamanya : memantau penggunaan semua resources; menerapkan aturan (policy); mengalokasikan resources yang diminta; mengambil kembali (dealokasi) resource
- Sumber daya pada komputer terdiri dari :
- Sumber daya fisik, misalnya : Keyboard, bar-code reader, mouse, joystick, light-pen, touch-screen, pointing devices, floppy disk drive, harddisk, tape drive, optical disk, CD ROM drive, CRT, LCD, printer, modem, ethernet card, PCMCIA, RAM, cache memory, register, kamera, sound card, radio, digitizer, scanner, plotter, dan sebagainya.
- Sumber daya abstrak, terdiri dari :Data dan Program
2. Sebagai Extended Machine (Virtual Machine), penyedia layanan
- Menyembunyikan kompleksitas / kerumitan pemrograman hardware dari programmer atau user.
- Menyajikan fasilitas yang lebih mudah dan sederhana untuk menggunakan hardware.
Konsep Sistem Operasi
1. Proses
- Proses adalah program yang sedang di-eksekusi.
- Proses terdiri dari : Executable program; program data dan stack; program counter; dll
- Pada sistem timesharing secara periodik sistem operasi menggilir eksekusi proses-proses yang ada, biasanya berdasarkan porsi waktu CPU.
- Ketika suatu proses dihentikan untuk sementara, maka proses tersebut harus dimulai kembali pada state yang sama dengan state ketika ia dihentikan.
- Semua informasi yang berkaitan dengan proses tersebut harus disimpan.Umumnya informasi tersebut disimpan pada tabel proses (array atau linked list), satu tabel untuk setiap proses.
- Tabel proses (process table) adalah tabel yang berisi informasi tentang semua proses yang dijalankan.
- Suatu proses terdiri dari : address space (core image) dan atribut / informasi pada tabel proses.
- System call utama dalam pengaturan proses adalah yang berkaitan dengan pembuatan dan pemberhentian suatu proses. Contoh :
- Command interpreter atau shell akan membaca command yang diketikkan user pada terminal, dan membuat proses yang menjalankan command tersebut.
- Bila telah selesai, maka proses akan menjalankan system call untuk menghentikan dirinya.
- Suatu proses dapat men-create proses lainnya yang disebut sebagai child process.
- Sistem operasi dapat berkomunikasi dengan suatu proses dengan menggunakan signal.
- Signal juga dapat digunakan untuk komunikasi antar proses.
- Pada sistem multiprogramming, setiap proses memiliki user identification (uid) yang berasal dari uid pemilik proses.
2. Files
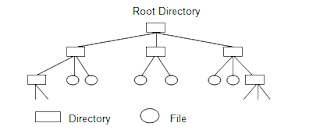
Terdiri dari : Pathname, Working directory, rwx (read, write, execute) bits protection code, File descriptor / handle, Special file (block & character), Standard input, Standard output, Standard error, Pipe. SO mendukung konsep direktori.
3. System Calls / API (Aplication Programming Interface)
- Suatu set tata cara pemanggilan di program aplikasi untuk memperoleh layanan system operasi. Berupa extended instructions / perluasan instruksi yang merupakan interface / layanan langsung antara program-program dengan sistem operasi.
- System calls meng-create, men-delete dan menggunakan objek-objek yang diatur oleh system operasi, antara lain : proses-proses dan file-file.
- Library procedure meletakkan parameter-parameter system call pada tempat tertentu dan memberikan instruksi trap untuk memulai sistem operasi
- Trap instruction : ketika diterima oleh sistem operasi, sistem memeriksa apakah parameter tersebut valid atau tidak
- Return form trap : sistem operasi mengembalikan kontrol ke library procedure
- Contoh mekanisme system calls untuk READ pada program C.
- count = read (file, buffer, nbytes)
4. Shell
- Shell pada Unix merupakan command interpreter yang walaupun bukan merupakan bagian dari sistem operasi, menggunakan banyak feature sistem operasi
- Prompt : standar input, menandakan bahwa shell siap menerima command
- Contoh :
- date
- date > file
- sort < file1 > file2
- cat file1 file2 file3 | sort > /dev/lp
- Background job : proses yang berjalan sementara user tetap bisa terus bekerja
Struktur Sistem Operasi
Sistem Monolitik
- Konsep : “Sistem operasi sebagai kumpulan prosedur dimana prosedur dapat saling dipanggil oleh prosedur lain di sistem bila diperlukan”.
- Kernel berisi semua layanan yang disediakan sistem operasi untuk pemakai.
- Contoh : Sistem Operasi Unix menggunakan konsep kernel loadable modules, yaitu :
- Bagian-bagian kernel terpenting berada dimemori utama secara tetap.
- Bagian-bagian esensi lain berupa modul yang dapat ditambahkan ke kernel saat diperlukan dan dicabut begitu tidak digunakan lagi diwaktu jalan (run-time).
- The ‘big mess’
- Tidak berstruktur
- Kernel call / supervisor call
- User mode
- Kernel mode / supervisor mode
Sistem Berlapis (Layered System)
- Konsep : “Sistem operasi dibentuk secara hirarki berdasarkan lapisan-lapisan, dimana lapisan-lapisan memberi layanan lapisan lebih atas”.
- Dimaksudkan untuk mengurangi kompleksitas rancangan dan implementasi system operasi. Tiap lapisan mempunyai fungsional dan antarmuka I/O antara dua lapisan bersebelahan.
- Contoh :
- Sistem Operasi THE (Technique Hogesschool Endiche), Djikstra, 1968.
- Sistem Operasi MULTICS (menggunakan concentric rings).
Sistem dengan Mesin Maya (Virtual Machines)
- Konsep : “Awalnya struktur ini membuat seolah-olah user mempunyai seluruh komputer dengan simulasi atas pemroses yang digunakan. Sistem operasi melakukan simulasi mesin nyata. Mesin hasil simulasi digunakan user, mesin maya merupakan tiruan 100% atas mesin nyata. Semua user diberi ilusi mempunyai satu mesin yang sama-sama canggih”.
- Contoh :
- Sistem operasi MS-Windows NT dapat menjalankan aplikasi MS-Dos, OS/2 mode teks, dan Win 16.
- Pengembang Linux membuat DOSEMU agar aplikasi MS-Dos dapat dijalankan di Linux, WINE agar aplikasi MS-Windows dapat dijalankan di Linux, iBCS agar aplikasi SCO-Unix dapat dijalankan di Linux.
- CP/CMS
- VM/370
- Virtual Machine Monitor
- CMS (Conversational Monitor System)
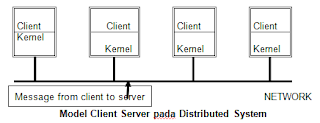
Sistem dengan Client-Server
Konsep : “Server adalah proses yang menyediakan layanan, dan Client adalah proses yang memerlukan / meminta layanan. Proses client yang memerlukan layanan mengirim pesan ke server dan menanti pesan jawaban. Proses server setelah melakukan tugas yang diminta, mengirim hasil dalam bentuk pesan jawaban ke proses client. Server hanya menanggapi permintaan client dan tidak memulai percakapan dengan client”.
Model Client Server pada distributed system
Sistem berorientasi objek
- Konsep : “Layanan diimplementasikan sebagai objek”.
- Model ini terstruktur dan memisahkan antara layanan yang disediakan dan implementasinya.
- Contoh :
- Sistem operasi X-kernel
- Sistem operasi MS-Windows NT telah mengadopsi beberapa teknologi berorientasi objek, tapi belum secara keseluruhan.
Layanan Sistem Operasi Komputer
- Layanan Otomatis : Alokasi sumberdaya; Catatan pemakaian; Proteksi; Penanganan kekeliruan; Pindah baris; Gulung jendela pada monitor
- Layanan permintaan pemakaian : Loading; Mengolah/run; Menyimpan/save; Menghapus/delete
Jenis Sistem Operasi
Aspek kegiatan
- Pemakai tunggal (single user)
- Pemakai jamak (multiuser)
Berdasarkan jenis-jenisnya
- Linux
- MS-Dos
- MS Windows-NT
- MS Windows
- Dll





2 comments
◾PROTOCOL SHIELDERS◾
ReplyHELLO,
I am COREY RODRIGUEZ by name,
the only GENERAL CEO of protocol-cyber-shield-hackers.
In this message, we will explain how you can almost avoid SCAMMERS and stay safe, plus how our organization works.
Read it carefully!!
Its reading will not take more than 10mins.
We kindly URGE you to not respond without have read the entire text. Those who mail without have read everything, ask questions that are answered here!!
⚠️WARNING:
MOST HACKERS YOU SEE HERE ARE FAKES
AND SIMULTANEOUSLY INCONGRUOUS !!.
It tears US up as we have received bitter emails of Jobs attempts proposals from most clients with hacking issues but never got it done and lost a lot in the process,
EXAMPLES OF LOSSES ARE:
➡️BINARY FUNDS,
➡️INVESTMENTS,
➡️LARGE SCALE FUNDS,
➡️PROPERTIES,
➡️STONES(JEWELRIES) etc....
all scammed by uncertified and fake hackers SIMPLY TERMED as "IMPERSONATION" like most you see here,
which is disappointingly inadequate,
leaving their mess for us to deal with eventually (WE DON'T MEAN TO BRAG ABOUT THAT).
SCAMMERS DON'T SHOW MERCY ON THEIR VICTIMS!
BY THE TIME YOU KNOW IT,YOU'VE GONE TOO DEEP BEING RIPPED OFF THROUGH DIVERSE TRICKY MEANS,PLEASE BE WISE ENOUGH TO PAY ATTENTION TO THIS ARTICLE AS YOU READ THROUGH IT.
HOW CAN YOU BE CAREFUL??
You won't know until you fall Victim ,but can be attentive to potential danger, error or harm if you take note of these:
1, you see uncertified email accounts carrying numberings like
"iamhacklord1232@(gmail,yahoo or hotmailDOTcom"
pls flee from them, BIG SCAMMERS.
They take your money and never do your job!!
2, you see posts like "do you need to spy on spouse?"
All fake!
just a way to lure you toward getting ripped OFF!.
3, posting fake testimonies and comments to trick you into feeling save and secured.
Pls endeavour to ignore!!
🛑NOTE: beware as we urge you not to make respond to any "IVAN HONG,PETER SANTOS,MONICA HART...(impersonating with our post pretending to work for us)
WE ONLY HAVE 2 EMAILS WHICH ARE LISTED BELOW THIS ARTICLE TO ATTEND TO YOU VARIOUS MANNER OF CYBER MISHAPS.
◾VERY IMPORTANT ◾
For years now, We've helped organizations secure data base, so many sites USES US AS SECURITY BACK UP TEAM BECAUSE OF OUR METHODS OF HANDLING CYBER MISHAPS.
🆗"CLEAR CRIMINAL RECORDS" 99%
🆗"iPHONE HACK" 99%
🆗"BINARY RETRIEVAL" 99% AND LOT MORE BEEN DONE IN SHORT TIMING!
these are significant EXPERIENCES & RECORDS a good and effectively fully recognized organization must firmly ascertain.
◾OUR "AIMS" HERE ◾
Are:
1◾to assign a qualified agent of specific rank to particularly any sort of cyber issues you intend dealing with in short and accurate timing.
2◾ to screen in real hackers (gurus only) in need of job with or without a degree, to speed up the availability of time given for Job contracts given to us.!!
Thus an online binary decoding exam will be set for those who seeks employment under the teams Establishment.
write us on:
◾ProtocolhacksATgmailDOTcom or
◾CybershieldnotchATgmailDOTcom
COREY ROD,
SIGNED...!
Thank you!!!
◾PROTOCOL SHIELDERS◾
ReplyHELLO,
I am COREY RODRIGUEZ by name,
the only GENERAL CEO of protocol-cyber-shield-hackers.
In this message, we will explain how you can almost avoid SCAMMERS and stay safe, plus how our organization works.
Read it carefully!!
Its reading will not take more than 10mins.
We kindly URGE you to not respond without have read the entire text. Those who mail without have read everything, ask questions that are answered here!!
⚠️WARNING:
MOST HACKERS YOU SEE HERE ARE FAKES
AND SIMULTANEOUSLY INCONGRUOUS !!.
It tears US up as we have received bitter emails of Jobs attempts proposals from most clients with hacking issues but never got it done and lost a lot in the process,
EXAMPLES OF LOSSES ARE:
➡️BINARY FUNDS,
➡️INVESTMENTS,
➡️LARGE SCALE FUNDS,
➡️PROPERTIES,
➡️STONES(JEWELRIES) etc....
all scammed by uncertified and fake hackers SIMPLY TERMED as "IMPERSONATION" like most you see here,
which is disappointingly inadequate,
leaving their mess for us to deal with eventually (WE DON'T MEAN TO BRAG ABOUT THAT).
SCAMMERS DON'T SHOW MERCY ON THEIR VICTIMS!
BY THE TIME YOU KNOW IT,YOU'VE GONE TOO DEEP BEING RIPPED OFF THROUGH DIVERSE TRICKY MEANS,PLEASE BE WISE ENOUGH TO PAY ATTENTION TO THIS ARTICLE AS YOU READ THROUGH IT.
HOW CAN YOU BE CAREFUL??
You won't know until you fall Victim ,but can be attentive to potential danger, error or harm if you take note of these:
1, you see uncertified email accounts carrying numberings like
"iamhacklord1232@(gmail,yahoo or hotmailDOTcom"
pls flee from them, BIG SCAMMERS.
They take your money and never do your job!!
2, you see posts like "do you need to spy on spouse?"
All fake!
just a way to lure you toward getting ripped OFF!.
3, posting fake testimonies and comments to trick you into feeling save and secured.
Pls endeavour to ignore!!
🛑NOTE: beware as we urge you not to make respond to any "IVAN HONG,PETER SANTOS,MONICA HART...(impersonating with our post pretending to work for us)
WE ONLY HAVE 2 EMAILS WHICH ARE LISTED BELOW THIS ARTICLE TO ATTEND TO YOU VARIOUS MANNER OF CYBER MISHAPS.
◾VERY IMPORTANT ◾
For years now, We've helped organizations secure data base, so many sites USES US AS SECURITY BACK UP TEAM BECAUSE OF OUR METHODS OF HANDLING CYBER MISHAPS.
🆗"CLEAR CRIMINAL RECORDS" 99%
🆗"iPHONE HACK" 99%
🆗"BINARY RETRIEVAL" 99% AND LOT MORE BEEN DONE IN SHORT TIMING!
these are significant EXPERIENCES & RECORDS a good and effectively fully recognized organization must firmly ascertain.
◾OUR "AIMS" HERE ◾
Are:
1◾to assign a qualified agent of specific rank to particularly any sort of cyber issues you intend dealing with in short and accurate timing.
2◾ to screen in real hackers (gurus only) in need of job with or without a degree, to speed up the availability of time given for Job contracts given to us.!!
Thus an online binary decoding exam will be set for those who seeks employment under the teams Establishment.
write us on:
◾ProtocolhacksATgmailDOTcom or
◾CybershieldnotchATgmailDOTcom
COREY ROD,
SIGNED...!
Thank you!!!
Posting Komentar